Gawds CTF/ Know whats in your head
28 Jan 2018Description
Try to see whats inside your head before moving forward.
This challenge was filled with dummy flags and was quite frustrating.
The Challenge
Looking at the description, it looks like the answer lies within the headers.

Like always, checking the robots.txt file, gave up the following info.
### BEGIN FILE ### User-agent: gawds-crawler Disallow: ### END FILE ###
From the robots.txt file, we can now infer that the User-Agent must be gawds-crawler.
Navigating to
http://swisshawk.ctf.gawds.in/flag
greets us with a Access Denied error.
Changing the method to POST also results in the same error.
I started to dig more.
I stumble upon sitemap.xml
This XML file does not appear to have any style information associated with it. The document tree is shown below. <urlset xmlns="http://www.sitemaps.org/schemas/sitemap/0.9"> <url> <loc>http://www.example.com/</loc> <lastmod>2018-01-02</lastmod> <changefreq>once</changefreq> <priority>0.8</priority> </url> <url> <loc> http://www.example.com/53129cdb3222c675a3ab1d3763a7665e90e26aed </loc> <lastmod>2018-01-02</lastmod> <changefreq>once</changefreq> <priority>1.0</priority> </url> </urlset>
Visiting
https://head.ctf.gawds.in/53129cdb3222c675a3ab1d3763a7665e90e26aed
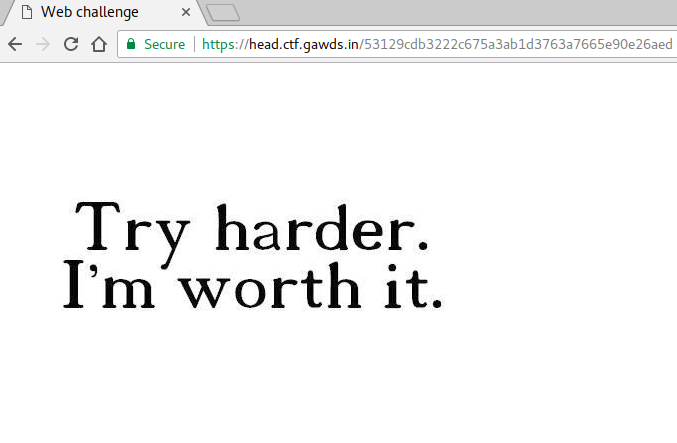
Checking the headers:
tryharderflag:flag{Alm0st_Reach4d_But_THis_is_A_DUmmY_Flag}
This was quite pissing off! I decided to give last and final shot.
Looking at the hash string, it seemed like a sha-1 hash.
So, I performed sha-1 hash of flag and obtained
112f3a99b283a4e1788dedd8e0e5d35375c33747
Visiting,
https://head.ctf.gawds.in/112f3a99b283a4e1788dedd8e0e5d35375c33747
You get:

When we check the headers, we get:
Flag: flag{G00d_W0rk_AlWys_check_f0R_headers}